IoT ecosystem and security
What is IoT ?
It is not easy to define the term Internet of Things (IoT). Indeed, there are a lot of different definitions, but IoT generally refers to scenarios where network connectivity and computing capabilities extend to objects, sensors and everyday items not normally considered as computers, allowing these devices to generate, exchange and consume data with minimal human intervention.
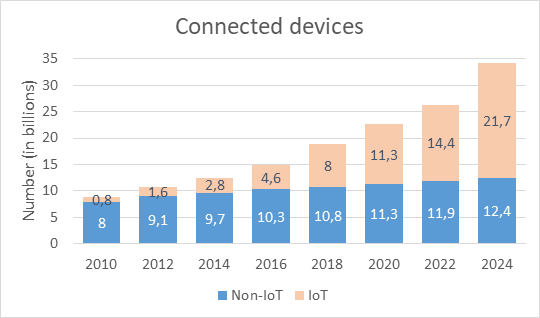
The concept of IoT started to gain in popularity in the 2010s thanks to Low-cost and low-power sensor technologies, increased connectivity, and cloud computing platforms. Today, we can find more than 14 billion connected IoT devices in the world.
With this come many challenges. Currently, there is no real homogeneity between protocols and manufacturers, and this is something that needs to be tackled. From a business point of view, we need to find the best compromise to create a cost-effective solution while taking into account all the questions related to privacy, security and safety.
We cannot speak about IoT without mentioning the 5G cellular network, as it will boost the IoT ecosystem even more thanks to some characteristics:
- Low latency: 5G will be able to deliver latency as low as 1 ms.
- Speed transmission: 5G will boost the speed transmission up to 10Gbps.
- Increased number of connected devices
- Network slicing: will enable the creation of subnetworks and with some specific characteristics, it will be possible to prioritise connections.
Typical architecture:
The simplified architecture of a typical IoT ecosystem looks like this:
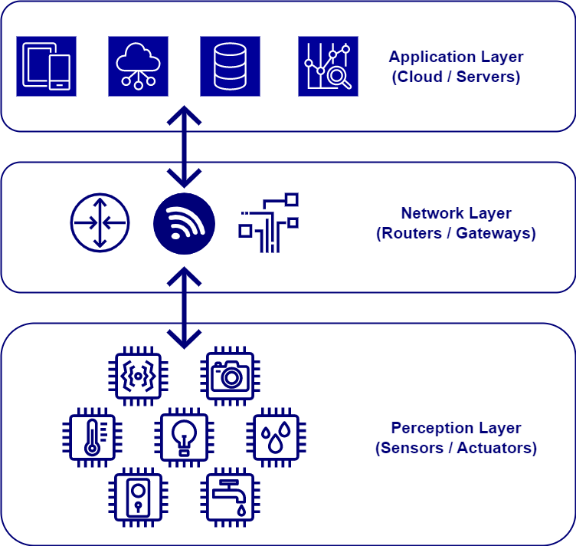
The perception layer contains all your devices that will interact with the real world. It will be your sensors, your vocal assistant, your connected fridge and everything you can imagine!
Then there is the network layer. There, we find different communications protocols like MQTT and COAP. They allow the communication between your different devices and your cloud platform.
Finally, there is the application layer in which you can find all your data. For example, the data will be stored and aggregated to monitor something or to use them for Artificial Intelligence (AI) purposes.
Use cases:
There are a lot of use cases that can be applied to IoT devices and for a lot of different sectors going from industry to healthcare. Let’s dive into some of them to see the concrete implications.
Healthcare:
It is more and more common to see IoT devices used for healthcare. Indeed, we can find pacemakers and insulin pumps. It is really useful because it enables easy monitoring, and warns healthcare services if necessary. Remote surgery will also be made possible thanks to the 5G and its low latency.
Transportation:
IoT will help having an efficient traffic management thanks to CCTV cameras. The data generated will help traffic management centres to keep a closer look on the vehicles. Smart parking, automated traffic light systems and smart accident assistance are some of the applications we can already find. Another application will be self-driving cars.
Agriculture:
IoT devices will help farmers close the supply demand gap, by ensuring high yields, profitability and protection of the environment. Drones can be used to enhance crop health assessment, irrigation, planting and field analysis.
Energy:
IoT applied to the energy sector can go from the distribution to the demand. It will help identify weak points and reinforce the energy grids accordingly to avoid any risks of blackout. It can also help obtain detailed information and identify areas to improve energy efficiency.
What are the risks of using IoT devices ?
As the number of IoT devices is constantly growing (see graph below), it creates many new possibilities, but with these come many cybersecurity risks.
So why are IoT devices vulnerable? This is quite simple:
IoT devices, due to their lack of built-in security, lack the basic security necessary to counter security threats.
We can distinguish some main threats:
- Too many different technologies
- Limited computer and hardware capabilities
- Vulnerable components
- Bad balance between cost and security
- User security awareness
IoT vulnerabilities:
Following the OWASP Top Ten vulnerabilities for IoT devices, we can mention some of the main vulnerabilities:
- Weak/hardcoded password: this is one of the most frequent methods used by attackers. Some already comprised passwords can be publicly available. Weak passwords can be easily bruteforced.
- Insecure network: attackers can benefit of weaknesses in the protocols and services, as well as unneeded protocols running on the IoT device. This is particularly susceptible to lead to man-in-the-middle attacks, where attackers will steal credentials or any other sensitive information.
- Insecure default settings: IoT devices can come with default settings that are unsecured. It can benefit attackers to gain access to the device and modify the configuration and in the worst case, launch bigger attacks.
- Use of insecure or outdated components: usage of deprecated components or libraries can allow the device to be compromised. This can go from the operating system to the use of third-party software or hardware components from a compromised supply chain.
How can IoT devices vulnerabilities affect users?
- Attackers can use the initial breach on the IoT device to go further into corporate networks, we call that lateral network movement.
- IoT devices can be used as a botnet. They are used to launch attacks like DDoS (distributed denial-of-network service) to make websites or services unavailable.
- We will also find more and more household devices like digitals assistants, health trackers and connected appliances. This could be dangerous for you, for example in the case of a health tracker but it can also be a new entry point if you work from home and let the attacker gain access to your corporate network.
- Attackers can exploit DNS vulnerabilities to launch DDoS attacks or to collect data from networks and connected devices, but also to introduce malware.
How to secure your IoT devices?
Securing IoT devices is not an easy task and must be done from the design phase to the end user of the solution.
Manufacturers must monitor and address vulnerabilities on their devices, by releasing patches and communicating to users when new patches are available. It is also important for them to include secured design and to conduct penetration testing to ensure no vulnerabilities will be remain once the device is released.
Users and organisations must keep their devices up to date, change default configurations to be more secure and of course, change default passwords. It is also important to monitor their systems to detect any unusual behaviour and malicious activities. Network segmentation and strong firewall policies, as well as having a complete inventory, are also an important component.
Conclusion:
As mentioned in this article, IoT is something that will take an important part in our lives. There is a lot of challenges around this, and we need to find a good balance to stay cost-effective and to add enough security into devices. Every sector can benefit from it, from the large companies to your personal usage. Cybersecurity will be one of the main important challenges and it needs to be taken into account from the manufacturer to the final user.
Written by Guillaume HOOREMAN & Florentin DELCOURT
Sources :
https://www.fortinet.com/resources/cyberglossary/iot-device-vulnerabilities
The Internet of Things: An Overview published by Internet Society in October 2015
https://www.thalesgroup.com/fr/europe/france/dis/mobile/inspiration/5g
Internet of Things (IoT) and the Energy Sector by Naser Hossein Motlagh, Mahsa Mohammadrezaei , Julian Hunt and Behnam Zaker published on the 19 January
https://www.iotsworldcongress.com/iot-transforming-the-future-of-agriculture/
https://owasp.org/www-pdf-archive/OWASP-IoT-Top-10-2018-final.pdf
https://www.conurets.com/5-major-applications-of-iot-in-transportation/#:~:text=IoT%20in%20transportation%20incorporates%20a,that%20data%20into%20useful%20information
https://iot-analytics.com/state-of-the-iot-2020-12-billion-iot-connections-surpassing-non-iot-for-the-first-time/
https://iot-analytics.com/internet-of-things-definition/