Business Continuity Management (BCM) and Cyber Resilience

“Why are they fundamental?”
One out of five companies has reported a ransomware attack in 2022 (+38% in 2022) among which two-third have paid the attackers. Hoping to retrieve their data, which strongly contributes to the recent ransomware pandemic.
Paying the ransom contributes to generate a vicious circle as it encourages criminals to continue their work, giving them more financial means. This financial windfall gives more possibilities to criminals who increase the scope of their attacks to make them more sophisticated, more devastating and more frequent.
To learn more about the fascinating world of ransomwares, check out the article Les rançongiciels: une arme en constante evolution we wrote earlier this month.
Regardless of the level of preparedness, a company (whatever its size) should regularly evaluate its incident response capabilities. This is even more topical in today’s high risk context. Not to mention, ransomware is not the only threat that may challenge resilience. An unforeseen event that disrupts business processes can always occur, being a natural disaster, power outage, fire, IT failure or cyberattack.
In this regard, the best resilience strategy is Business Continuity Management (BCM). Having a solid BCM in place is essential for any company since it provides the adequate solutions to continue to operate during and after a disaster or disruption. It also minimises the downtime and financial losses.
Business Continuity Management
The BCM lifecycle is usually divided into four steps:
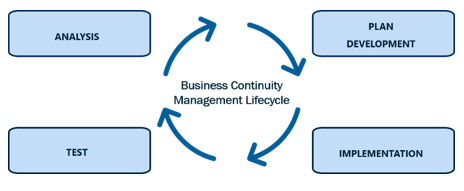
1. Analysis
The analysis phase aims at identifying and prioritising critical business functions, identifying their potential risks, establishing a crisis management unit and drafting a Business Impact Analysis (BIA) by determining financial and operational impacts on the organisation for each disruption scenario. To fully serve its purpose, the BIA must also identify the businesses’ resources and their dependencies which have to be taken into account when prioritising their recovery order. The BIA introduces two new crucial concepts:
- Recovery Point Objective (RPO)
When a disaster occurs, it is very likely that some data will be lost. To avoid that, businesses should store copies of their data in isolated locations. This way, if one copy is compromised because of a disaster, the data still exists somewhere else. This practice is known as backups and a business can choose how often they want to save a new copy of their data. The more frequent the backups, the more recent the backup version and so the smallest amount of data to lose.
For instance, a business might decide it cannot lose more than one hour of financial data, but it can lose up to one week of marketing data. This amount of data lost before the disaster occurred is what is called the RPO.
- Recovery Time Objective (RTO)
Unlike the RPO which looks back from the disaster, the RTO looks forward. A disaster often disrupts the availability of stored data and of processing facilities in a way that can be very significant (e.g. a backup datacenter can take hours to take over).
Businesses should define how long they can afford to lose access to each type of data and each process.
For instance, a bank might require no more than a few minutes of downtime on their system that authorizes payments, but allow their customer data to be unavailable for a few hours. This maximum amount of time of unavailability is called the RTO.

Note that the shorter the RPO and RTO, the more expensive it becomes to operate. Therefore, businesses have to carefully define them for each of their data and process, and look for the best tradeoffs between cost and risk.
2. Plan Development
Drafting a Business Continuity Plan (BCP) will enable outlining the procedures and resources that an organisation will use to continue critical processes in the event of a disaster or disruption.
3. Implementation
The Disaster Recovery Plan (DRP) is a sub-part of the BCP, it is initiated when a disaster occurs and the BCP is activated. It explains how to support critical business processes on a second functioning infrastructure. Then how to recover from the disaster and have all of the processes running again as in the initial state (which is the very definition of resilience).
4. Test phase
It is probably the most arduous stage to complete. It involves the crisis management unit, as well as IT teams for the testing of the BCP and the DRP through tabletop and simulation exercises.
Effective communication is also crucial for BCM. This includes having clear, concise communication channels in place for both internal and external stakeholders. As BCM is an ongoing process (not just a one-time effort), it is important to regularly review and update the plan to ensure it remains effective and relevant.
Overall, BCM is an essential part of any company’s operations. By proactively planning and preparing for potential disruptions, businesses can minimise the impact of disasters and keep their operations running smoothly.
Antoine Bricogne, François Gilet, Allan Lallemand and Anisa Skenderovic
Sources:
- The Hiscox Cyber Readiness Report 2022 | Hiscox UK
- https://www.darkreading.com/attacks-breaches/check-point-research-reports-a-38-increase-in-2022-global-cyberattacks
- https://www.blogdumoderateur.com/ransomwares-entreprise-chiffres-cles-conseils-premunir/
- https://www.welivesecurity.com/2022/04/01/cybersecurity-survival-tips-small-businesses-2022-edition/
- https://www.welivesecurity.com/2020/08/07/small-medium-sized-businesses-big-targets-ransomware-attacks/
- https://www.upguard.com/blog/what-is-ransomware-as-a-service#:~:text=Ransomware%20as%20a%20service%20(RaaS)%20is%20a%20subscription%2Dbased,Service%20(SaaS)%20business%20model
- https://www.gpomag.fr/web/etudes/ransomware-pme
- https://www.wwt.com/topic/cyber-resilience/overview
- What is Recovery Point Objective (RPO) | Imperva