

Industroyer 2 : the Russian Cyberattack on Ukraine Infrastructure
Summary
Critical infrastructure services of Ukraine have been the target of a cyberattack, before and after the invasion of Russia. It seems that attackers still launch more attacks. The last one was an energy supplier in Ukraine.
The attack Campaign has tempted to deploy a new malware named Industroyer2. This malware is capable of damaging or disrupting the ICS (Industrial Control System) of the target. This operation was targeting an Electric substation. The Ukrainian Computer Emergency Response Team, Microsoft and the cybersecurity company called ESET are analysing this attack.
The likely culprit is the Sandworm threat group operating under Russian intelligence orders GRU. Here is a diagram presenting the different malwares used during this attack:
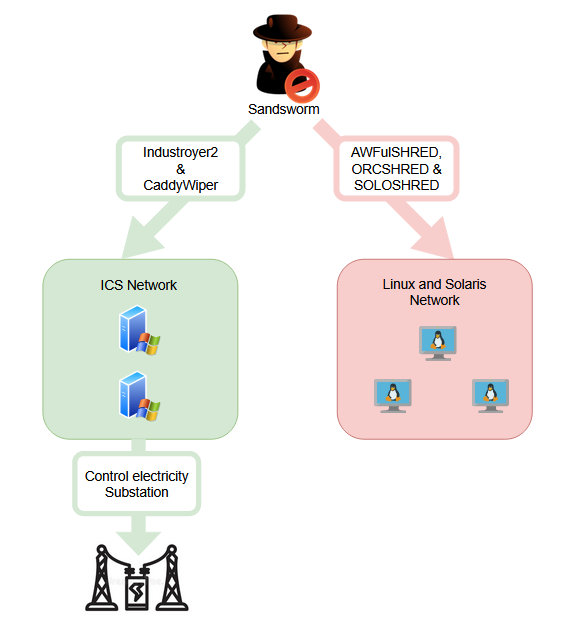
An introduction about Industroyer
Industroyer2 is the evolution of the Industoyer malware.
Industroyer is a malware designed to interfere the industrial control systems process, especially the one used in electrical substations. This malware has been used in the cyberattack on Ukraine’s power grid in 2016. This attack had cuts off the power of the capital. It is important to mention that it is the first known malware designed to attack electrical grids.
This malware supports four different ICS protocols:
- IEC 60870-5-101 (aka IEC 101)[1]
- IEC 60870-5-104 (aka IEC 104)[2]
- IEC 61850[3]
- OLE for Process Control Data Access (OPC DA)[4]
This was how the attacker proceeds:
After installing a main backdoor that can install additional backdoor, it authenticated itself to a local proxy over the internal network. Then an HTTP channel to an external C&C server (Command and control) hidden in the TOR network was opened.
After that, the additional module and command were transferred. The backdoor created a file in the local system but the content could not be reconstructed because a Data Wiper was used to:
- Delete all the registry keys that are associated with the system
- Overwrite:
- Control network configuration files on all hard drives and network drives.
- All generic windows files.
Moreover, this backdoor overwrote an existing service and referred itself as a new service in order to establish persistency in the system as it would be loaded automatically after rebooting.
Industroyer 2
It is malware that use logic bomb functionality; it has been deployed on target machines as a Windows executable and it was scheduled to be executed on April 8.
This malware has an IEC-104 protocol module (IEC 60870-104) meaning it can communicate with protection relays in electrical substations. The “International ElectroTechnical Commission” released this protocol in 2000. This standard is a Network access for IEC 60870-5-101 using standard transport profiles meaning that he enable connexion between the substation and the control station using TCP/IP.
In order to carry out its attack, the Sandsworm group used, in addition to Industroyer 2, other malware families such as « CaddyWiper », « ORCSHRED », « SOLOSHRED » and « AWFULSHRED ».
The Windows executable named “108_100.exe” had instructions to launch on April 8, 2022, precisely at 16:10 UTC.
Industroyer from 2016 was a modular platform with payloads for several ICS protocols. Conversely, Industroyer 2 only uses the IEC-104 protocol also knows as IEC 60870-5-104 to communicate with industrial equipment. This protocol is traditionally used for communicating with electrical relays. It is also able to communicate with several machines at the same time.
Industroyer2 shares many code similarities with the 2016 Industroyer’s payload 104.dll. This malware is strongly believed to have been created using code from its predecessor.
The creators of this malware did not hide its activity, the configuration is not protected in the executable given that we cannot find any form of obfuscation. The configuration analysis shows us that the attackers have a good knowledge of the target environment including security policies.
This malware is highly configurable. It contains hard coded configurations into its code that drives the actions of the malware and it contains a list of Information Object Addresses (IOAs) in order to change the state of remote station associated with these one. IOAs identify a specific data element of a device that can be power line switches or circuit breakers in an RTU or relay configuration.
This shows us two information about this malware:
- The attacker had a very good knowledge of the target Operational Technology environment.
- Industroyer2 has been designed to be executed in an environment with privileged access to the target device
For its predecessor Industroyer, the configurations were stored in a separate file named “%CONFIGURATION%.ini”.
It is important to mention that for Industroyer2, the attacker must recompile the code for each new victim or environment. In the case of the Ukrainian attack the code has been compiled on March 23rd, 2022, which lets us understand that the attacker planned his target for more than 2 weeks ahead of the execution.
The new configuration format is stored as a string, which is supplied to the malware’s IEC-104 communication routine. The configuration contains values like Application Service Data Unit address, information object addresses, timeouts etc.
Industroyer2 terminates a legitimate process used in standard operations and then connects to the targeted devices. He also renames the legitimate application and add “.mz” to the name in order to prevent automatic restart of the process.
The analysis process is still ongoing for this malware to deep dive in understanding it despite some difficulties. In fact, Industroyer2 produce a log file of its progress but unlike its predecessor, this produce output with various error codes in order to hamper the analysis.
The attacker also tried to hide its activities using a wiper.
CaddyWiper
Sandsworm also deployed another malware with Industroyer2, a new version of CaddyWiper.
The purpose of this was:
- To slow down the recovery process
- Prevent operators of the energy company to regaining the control of ICS
- To cover their tracks
This new version uses a new loader named ARGUEPATCH by CERT-UA. It is a patched version of a legitimate component Hex-Rays IDA Pro software.
The researcher still do not know why they chose to hide this piece of software in it.
Recommendation
To protect OT systems, here are some recommendations to be implemented:
- Implement network segmentation in order to separate OT subnet and IT subnet.
- Implement basic security rules: Change password at regular’s intervals, Check the identity access for each employee, Implements pentest.
- Use YARA[5] rules : YARA rules are available on Github to detect the use of some malware family used in the attack like AWFulSHRED, ORCSHRED, POWERGAP and SOLOSHRED.
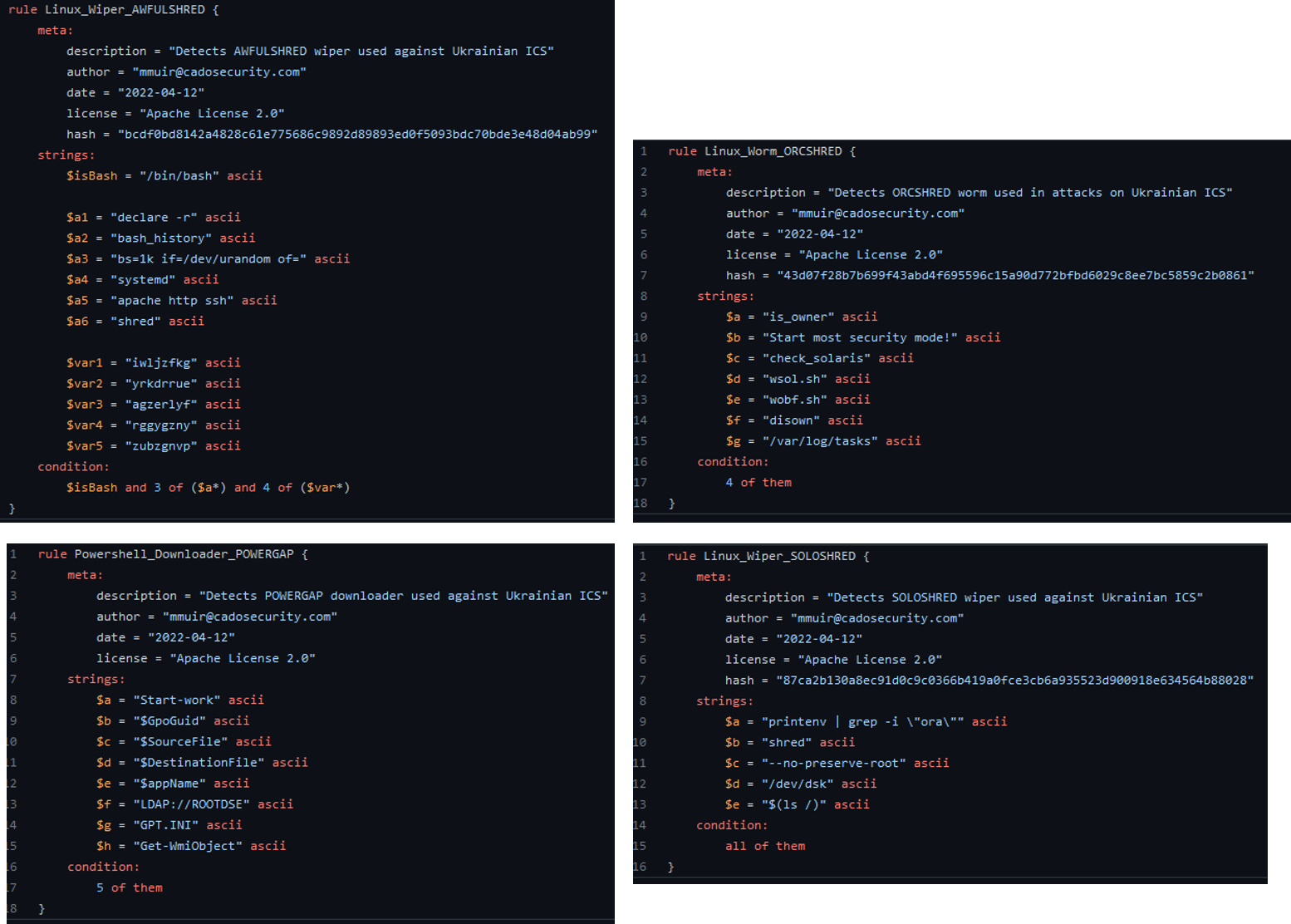
- Use detection tools and automated Firewall: To detect irregularities and anomalies in the network and OT environments.
- Threat hunting and vulnerability hunting
- Update software, Operation system, application and firmware on IT network assets.
- Use Multi factor Authentication and add security to the authentication with strong password policies.
- Provide end-user awareness and training to prevent phishing and social engineering and spear phishing campaigns.
- Create, maintain and exercise cyber incident and response withBCP, DRP for the resilience of service.
- Encrypt all backup data
- Implement audit to identify new weakness within systems.
- Use EDR programs to detect threat behaviour and block them
- Disable all unnecessary ports and protocols.
Written by Ganesh PAJANI and Paul PEIX
[1] https://webstore.iec.ch/preview/info_iec60870-5-101%7Bed2.0%7Den.pdf
[2] https://webstore.iec.ch/preview/info_iec60870-5-104%7Bed2.0%7Dfr_d.pdf
[3] https://en.wikipedia.org/wiki/IEC_61850
[4] https://en.wikipedia.org/wiki/OPC_Data_Access
[5] https://www.varonis.com/blog/yara-rules
Sources:
https://www.welivesecurity.comsu/2022/04/12/industroyer2-industroyer-reloaded/
https://www.enigmasoftware.fr/industroyer2malware-supprimer/
https://www.welivesecurity.comsu/2022/04/12/industroyer2-industroyer-reloaded/
https://www.enigmasoftware.fr/industroyer2malware-supprimer/
https://rhebo.com/en/service/glossar/industroyer-25114/
https://www.netresec.com/?page=Blog&month=2022-04&post=Industroyer2-IEC-104-Analysis
https://github.com/cado-security/DFIR_Resources_Industroyer2/blob/main/YARA/SOLOSHRED.yara
https://www.nozominetworks.com/blog/industroyer2-nozomi-networks-labs-analyzes-the-iec-104-payload/
https://query.prod.cms.rt.microsoft.com/cms/api/am/binary/RE4Vwwd
https://www.mandiant.com/resources/industroyer-v2-old-malware-new-tricks
https://malpedia.caad.fkie.fraunhofer.de/details/win.industroyer2
https://www.ipcomm.de/protocol/IEC104/en/sheet.html
https://www.cisa.gov/uscert/ncas/alerts/aa22-110a
https://rhebo.com/en/service/glossar/industroyer-25114/
https://www.netresec.com/?page=Blog&month=2022-04&post=Industroyer2-IEC-104-Analysis
https://github.com/cado-security/DFIR_Resources_Industroyer2/blob/main/YARA/SOLOSHRED.yara
https://www.nozominetworks.com/blog/industroyer2-nozomi-networks-labs-analyzes-the-iec-104-payload/
https://query.prod.cms.rt.microsoft.com/cms/api/am/binary/RE4Vwwd
https://www.mandiant.com/resources/industroyer-v2-old-malware-new-tricks
https://malpedia.caad.fkie.fraunhofer.de/details/win.industroyer2






